Dont Be That One. Shred any documents with personal or financial information on them.
Join a Plan Today.

. Find Your Area Of Interest With Our Category List And Expand Your Horizons. However these have some limitations in the m-commerce. Proof of your address mortgage statement rental agreement or utilities bill Any other proof you have of the theftbills Internal Revenue.
The wide range of cybercrime investigated by private agencies knows no limits and includes but is not limited to hacking cracking virus and malware distribution DDoS. As technology advances so do the techniques used by identity thieves. A government-issued ID with a photo.
CIPPIC 2007 Identity Theft. Ad Credit Monitoring Can Help You Detect Possible Identity Fraud Sooner And Prevent Surprises. Notify the credit bureau in writing of any questionable entries.
Ad A Free Online Course On Protecting Yourself From Identity Theft. Get Started By Signing Up. Safeguard Your People Data and Infrastructure Using Microsoft Solutions.
INTRODUCTION In order to prevent detect and deal with the aftermath of identity theft it helps to have an understanding of how it. See our ID Protection Reviews Find Who Is Rated 1. Canadian Internet Policy and Public Interest Clinic.
Identity ID theft happens when someone steals your personal information to commit fraud. Safeguard Your People Data and Infrastructure Using Microsoft Solutions. Identity thieves do this in order to intercept credit card offers then apply for a credit card in your name without your knowledge.
Get Protection from Identity Theft. Introduction and Background CIPPIC Working Paper No1 ID Theft Series March 2007 Ottawa. The FBI is seeking victims whose personally identifiable information PII may have been misused between September 2018 and.
Free Monitoring Of Your Experian Credit Report With Alerts When Key Changes Occur. Ad Have Full Control of Your Credit Activity. If this has happened at your address inform.
The identity thief may use your information to apply for credit file. Ad An Identity Solution That Works For All Your Users Apps and Devices. IDShield Offers Affordable Plans Designed For Ultimate Protection.
Review a copy of your credit report at least once each year. Online organisations commonly use electronic commerce approaches. Compare Identity Theft Protection Reviews.
First file the theft with the Federal Trade Commission FTC and receive an identity theft affidavit which you will then take when you file the crime with the local police and get a police report. Seeking Victims in Identity Theft Investigation. Identity Theft happens to 1 Out of 4.
This paper presents an evaluation of the. Ad Affordable Plans Designed For Ultimate Protection. The threat of identity theft is on the rise.
The Identity Theft File developed by NCIC serves as a means for law enforcement to flag stolen identities and identify imposters encountered by law enforcement personnel. Ad An Identity Solution That Works For All Your Users Apps and Devices. CIPPIC Working Paper No2 Techniques of Identity Theft 1.
Be Safe from Fraudulent Transactions Loans. Ad Best Identity Theft Protection Services 2022.
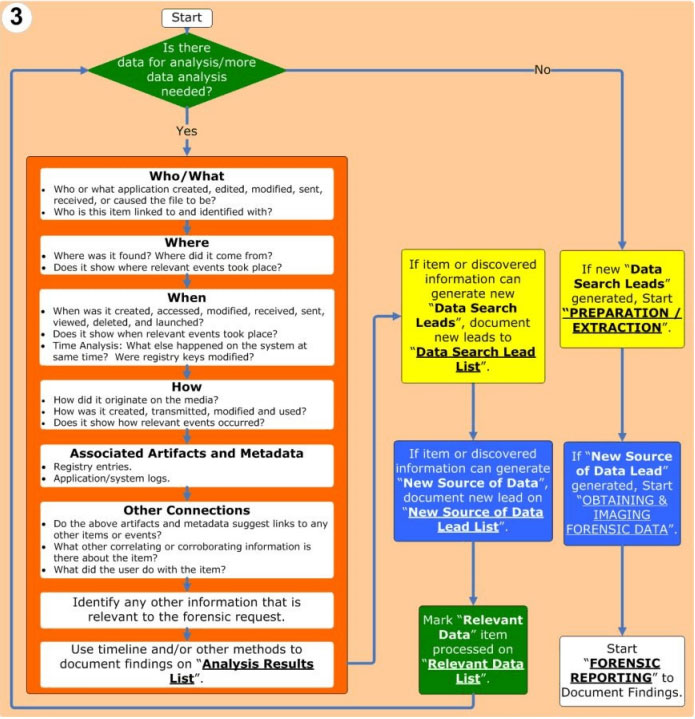
Computer Forensics Digital Forensic Analysis Methodology

Cyber Crime Investigation Making A Safer Internet Space

Pdf Online Id Theft Techniques Investigation And Response

Tips And Advice To Prevent Identity Theft Happening To You Europol

Identity Theft Investigations Pinow Com

Pdf Identity Theft Identity Fraud And Or Identity Related Crime


0 comments
Post a Comment